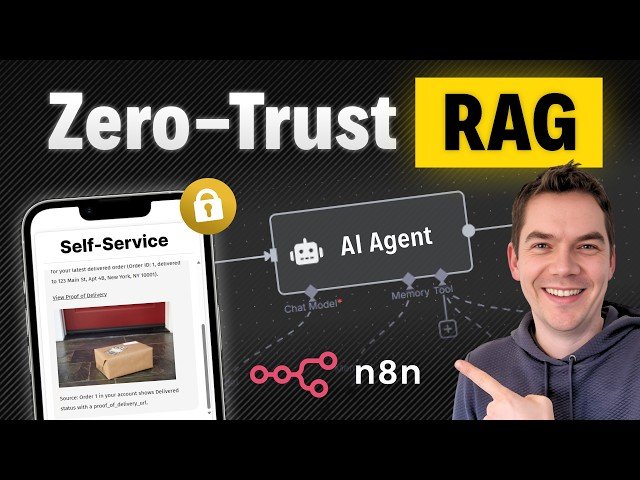
Building Personalized AI Agents: Most AI tutorials focus on generic responses, overlooking the need for user-specific data handling. Ensuring Security: The video explains multi-user AI architecture requires stringent security to prevent data breaches when handling customer-specific inquiries. E-commerce Application: Demonstrates a self-service AI agent integrated into a WooCommerce store, emphasizing data isolation and tailored responses. Implementation Strategies: Seven strategies are shared to enforce data isolation, including using JWTs, RLS in databases, and proxy servers. Advanced Shielding Techniques: Different approaches to securing data in multi-user scenarios, from proxy servers to database-enforced security and multifactor authentication.
Quotes:
The key isn’t just building the agent, it’s the security.
Get this wrong and you’ve just built a major data breach just waiting to happen.
The problem with this approach is that now, if you go to the headers, you can actually see the authorization.
Statistics
| Upload date: | 2025-08-19 |
|---|---|
| Likes: | 618 |
| Comments: | 28 |
| Fan Rate: | 2.13% |
| Statistics updated: | 2025-09-18 |
Specification: I Deployed a Secure Multi-User AI Agent in n8n
|